
Threat intelligence enriched with External Attack Surface Management, Brand Protection, and Dark Web Radar.
Protect your business from the dangers lurking in the hidden corners of the internet.
Effective threat hunting and threat actor tracking with behavioral analytics.
Discover your assets with a hacker mindset.
Stay ahead of threat actors with actionable intelligence alerts.
Evaluate the security posture of your entire supply network.
Your guide in harnessing the full potential of our platform.
Hear SOCRadar’s impressive achievements from our clients.
Automate and operationalize your security operations.
Consulting and professional services for cybersecurity excellence.
Industry, sector, and region-based in-depth research.
Discover the heartbeat of cyberspace through a collection showcasing the latest incidents.
Discover how XTI empowers organizations to proactively identify, mitigate, and respond to evolving cyber threats.
Register for our live webinars, and watch our on-demand webinars instantly.
Dive deep into the world of cyber threats, advanced analysis techniques, and cutting-edge strategies.
Stay informed and up-to-date on the latest cybersecurity trends.
Explore SOCRadar’s learning experience to fuel your cybersecurity journey with insights that exceed industry standards.
We offer expert-led, and exclusive trainings to help you master the latest in cybersecurity, trusted by over 2,000 top companies.
Scan the dark web to prevent your leaks from turning into real risks.
Instantly access dark web findings about your organization’s assets.
Check if there is anything about you in SOCRadar’s ever-expanding breach database.
Track threat actors and groups by country or industry for effective follow-up.
Explore threat actors’ tactics, techniques, activities, and detailed profiles targeting your industry or region.
All-in-one next-generation tools for investigating everyday events like phishing, malware, account breach, etc.
Power your search with SOCRadar’s IOC Radar.
Let’s get to know each other better.
Broaden your market reach and increase ARR with SOCRadar Extended Threat Intelligence.
Get informed of our upcoming events.
Latest news about our platform, company, and what’s being said about us.
Begin an extraordinary journey in your professional path with SOCRadar.
We’d like to hear from you.
SOCRadar Training Series – Mastering AI in Cybersecurity From Theory to Practice
Resources
[Update] August 31, 2023: See the subheading: “LockBit’s Operational Struggles, Empty Threats, and Sudden Surge.”
[Update] July 03, 2023: LockBit claimed to hack Taiwan Semiconductor Manufacturing Company (TSMC), but TSMC clarified that only one of its suppliers, Kinmax Technology, was breached. Added the subheading: “TSMC Confirms Supplier Hack Following Lockbit’s Claim.”
[Update] June 23, 2023: LockBit is reportedly developing ransomware capable of targeting a broader range of systems, added the subheading: “LockBit Tries to Expand Reach to Different Architectures: Apple, Linux, FreeBSD.”
[Update] June 15, 2023: LockBit was identified as the most active global ransomware group and RaaS provider based on the number of victims on their data leak site. Added under the subheading “The Most Active Ransomware Group of 2022: LockBit.”
The frequency of ransomware attacks is on the rise every year. A single group, the LockBit Ransomware Group, is accountable for over one-third of all ransomware attacks in the latter half of the previous year, the initial quarter of 2023.
LockBit Ransomware Group was first observed in September 2019, it became the most active ransomware group of 2022 with the shutdown of Conti, and as of the first quarter of 2023, they still stand out as the most active ransomware group. The group, which has over 1500 victim announcement records on the SOCRadar platform, broke the record in the first quarter of 2023 as the most active ransomware group by far, with over 300 announced victims.
Atento, a CRM company, showed the impact of an attack by LockBit as $42.1 million in its financial performance report published in 2021. $34.8 million was due to revenue loss, and $7.3 million was mitigation expenses. Even if these astronomical numbers could vary from company to company, the total financial loss caused by LockBit’s malicious acts can exceed billions of dollars.
Security researchers also have found new strains and evidence that the group responsible for LockBit 3.0 plans to expand the malware’s infection capacity. While the latest variant LockBit 3.0, had previously targeted Windows, Linux, and VMware ESXi servers, alleged new versions of LockBit encryptors have been identified that can also affect macOS, ARM, FreeBSD, MIPS, and SPARC CPUs. Given the group’s already sizable attack volume, it is likely that they will continue to increase the number of target devices, which could result in a significant surge in LockBit attacks soon.
LockBit 3.0 is a Ransomware-as-a-Service (RaaS) group that continues the legacy of LockBit and LockBit 2.0. From January 2020, LockBit adopted an affiliate-based ransomware approach, where its affiliates use various tactics to target a wide range of businesses and critical infrastructure organizations. LockBit has been highly active in deploying models such as double extortion, initial access broker affiliates, and advertising on hacker forums. They have even been known to recruit insiders and make contests in forums for recruiting skilled hackers; such expansionist policies have attracted numerous affiliates, have victimized thousands of entities, and continue their malicious acts.
LockBit Black, also known as LockBit 3.0, has been recalled as the latest variant of LockBit since July 2022. One of the key differences from its predecessor is the ability to customize various options during both the compilation and execution of the payload. LockBit 3.0 utilizes a modular approach and encrypts the payload until execution, which presents significant obstacles to malware analysis and detection.
LockBit 3.0 infects the target system if it is not on the exclusion list of specific languages. Excluded languages include the local language of Russian-influenced countries and the languages of Russian-allied countries.
To confirm the location of the targeted system, LockBit ransomware employs the functions:
It cross-checks the result against a set of countries, and in case the locale doesn’t match any of the specified countries, the malware proceeds to the subsequent verification step. Some of the languages that are excluded are Romanian (Moldova), Arabic (Syria), and Tatar (Russia), but this is not an exhaustive list.
Although the ransomware group claims not to engage in politics, many of its targets appear to be NATO and allied countries. According to SOCRadar data, about half of the attacks with the LockBit 3.0 variant affect US companies.
Again, according to SOCRadar data, manufacturing takes the lead on a sectoral basis, but it is impossible to identify a specifically targeted industry. The fact that healthcare and education are among the sectors they target the most reveals that no industry is excluded, and in terms of business type. However, it is seen that it usually targets small or medium-sized organizations; huge companies such as IT company Accenture can also fall into the victim category for LockBit.
According to CISA’s advisory:
LockBit 3.0, a Ransomware-as-a-Service (RaaS), has several options for configuring its behavior during compilation. Once executed in a victim’s system, LockBit 3.0 affiliates can modify its behavior using additional arguments, such as lateral movement or safe mode. If LockBit affiliates lack access to the passwordless version of the ransomware, they must provide a password during execution. Provided cryptographic key decodes the ransomware’s executable to protect the encoded file uploaded to the target system.
LockBit 3.0 affiliates use diverse methods for initial access, including exploiting RDP, launching phishing campaigns, and exploiting vulnerabilities in public-facing applications. Using an open-source package installer known as Chocolatey to install and execute malicious payloads is a recurring feature in LockBit 3.0 attacks, likely employed to evade detection.
LockBit 3.0 uses hardcoded credentials or compromised local accounts with elevated privileges to spread through a victim network. Using the Server Message Block (SMB) protocol, it can also spread via Group Policy Objects and PsExec. After encryption, LockBit 3.0 drops a ransom note and changes the host’s wallpaper and icons to LockBit branding. It may also send encrypted host and bot information to a command and control server.
LockBit 3.0 affiliates exfiltrate sensitive company data files before encryption using Stealbit, rclone, -exfiltration tools that LockBit commonly uses- and public file-sharing services. Their affiliates also use other public file-sharing services to exfiltrate data. LockBit threat actors use various tools such as ProDump and SoftPerfect Network Scanner to collect information about hostnames, network services, and remote access protocols. They also use remote desktop software, popular file transfer tools, and PuTTY Link to move between hosts and transfer files between compromised hosts and their command and control servers.
LockBit ransomware deletes log files, files in the recycle bin, and volume shadow copies after encrypting the victim’s files. The group also employs a hybrid encryption approach using AES and RSA encryption algorithms.
The LockBit group is responsible for approximately one in six ransomware attacks targeting U.S. government offices in 2022, according to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), FBI, and other cybersecurity authorities.
In a collaborative effort, the agencies published an extensive examination of LockBit, which is considered the most widely deployed ransomware variant worldwide, in 2022.
LockBit Conducted Nearly 1,700 Attacks and Gained $91 Million from Victims in the US
The agencies disclosed that LockBit had claimed responsibility for at least 1,653 ransomware attacks by listing the victims on its leak site, and since the first attack in the U.S. in January 2020, the group has extorted approximately $91 million from its victims in the United States.
Each participating country shared statistics showcasing LockBit’s prevalence in their respective regions. For example, Australia reported that the gang accounted for 18% of total reported ransomware incidents in the past year. LockBit was responsible for over 20% of attacks in Canada and New Zealand in 2022.
In the U.S., LockBit targeted public entities, including municipal and county governments, public education institutions, and emergency services such as law enforcement agencies, constituting 16% of attacks.
The advisory on CISA outlines LockBit’s tactics and exploited vulnerabilities, highlighting the group’s utilization of affiliates who employ diverse methods to breach organizations. Some affiliates have also leveraged popular vulnerabilities like Log4j.
Operating as a Ransomware-as-a-Service (RaaS), LockBit attracts affiliates to conduct a variety of ransomware attacks. Additionally, CERT NZ observed LockBit affiliates engaging in secondary ransomware extortion by targeting organizations responsible for managing other networks. After infecting the primary target, affiliates proceed to extort customer companies using secondary ransomware, locking down the services they use. These findings emphasize LockBit’s widespread reach and the decentralized network of threat actors involved in these attacks.
LockBit has continuously improved its operations, evolving through multiple versions since LockBit Red, such as LockBit 2.0 and LockBit 3.0 (LockBit Black). The group integrated tooling from other ransomware strains, such as BlackMatter and ALPHV (BlackCat Ransomware), into LockBit 3.0. In January 2023, LockBit released LockBit Green, incorporating source code from the ended Conti ransomware.
Cybersecurity experts have noted LockBit’s distinctive approach in consistently enhancing its model. The introduction of LockBit 2.0 in mid-2021 had an immediate impact on the cybercriminal market.
LockBit is reportedly developing ransomware capable of targeting a broader range of systems, extending beyond the Windows environment.
Researchers from Kaspersky recently discovered a ZIP file containing LockBit malware samples that targeted FreeBSD, Linux, and various embedded technologies, including diverse CPU instruction set architectures, including ARM, MIPS, ESA/390, PowerPC, and even the Apple M1 chip utilized in Mac and iPad devices.
Researchers state that these samples originate from LockBit’s earlier encryptor variations, which threat actors used when targeting VMWare ESXiservers. However, the samples are still being developed as some are unsigned and cannot be executed yet.
Still, the fact LockBit is trying to develop such ransomware signifies a growing trend among ransomware actors to expand their target platforms. If released, these new ransomware variants could present new challenges for victims and further establish LockBit’s position in the evolving threat landscape.
Taiwan Semiconductor Manufacturing Company (TSMC) confirmed that one of its hardware suppliers was hacked, but assured that it had no impact on its operations or customer data.
The group demanded a $70 million ransom from TSMC, but there were no indications of any plans to pay.
The supplier, Kinmax, acknowledged the breach in its internal testing environment, which contained system installation preparations for customers. TSMC promptly terminated data exchange with Kinmax following the breach.
Kinmax has apologized to affected customers and implemented enhanced security measures to prevent future incidents.
The cybersecurity realm has been engaged in discussions concerning LockBit’s predicament for a while now. Researchers have reported that there are operational challenges within the ransomware gang.
The gang’s challenges have led to a noticeable decline in the quality of their ransomware activities. Nonetheless, the notorious gang continues to project a facade of strong narratives in their communication.
However, despite maintaining their facade, the researchers’ observation holds true – LockBit has consistently stumbled in their attempts to actually release the stolen data. This disconnection between their claims and actions has led to the conclusion that their threats were hollow, relying solely on their infamous reputation to pressure victims into paying ransom.
As these discussions persist, a recent turn of events has come to the fore. After a period of relative inactivity spanning several months, the LockBit ransomware group has listed more than 20 victims within a single day.
The latest tweet from vx-underground not only confirms this surge in activity but also highlights that the gang has reindexed their entire website. As of August 31, 2023, the revamped site now lists over 100 previous victims whose data has supposedly been leaked.
As these leaks emerged subsequent to claims about LockBit’s struggles, it almost appears as if the gang is trying to disprove the assertions and mitigate their impact on the gang’s reputation.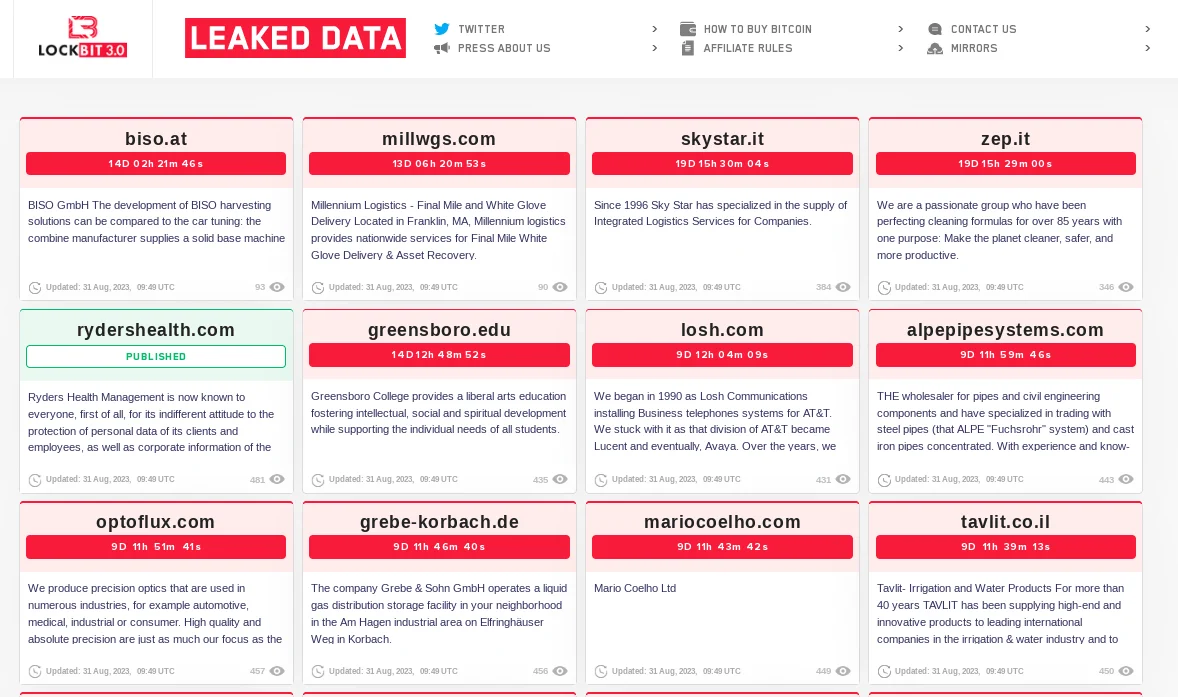
LockBit’s latest leaks
In conclusion, LockBit 3.0 is a highly active and expanding Ransomware-as-a-Service (RaaS) group that has victimized thousands of organizations worldwide and employs various tactics, techniques, and procedures due to its wide number of affiliates. Moreover, there is a high probability that the number of victims and target pool will keep increasing, leading to a notable upsurge in LockBit attacks in the upcoming days, especially if they manage to become the first notable ransomware affecting IOS devices. The group’s targeting of many countries and sectors, and its efforts to increase the number of systems it can infect, also show that it poses a significant danger to all organizations.
LockBit affiliates commonly use phishing campaigns to gain initial access to their ransomware attacks. To prevent this, organizations can use SOCRadar’s Digital Risk Protection for brand protection, which proactively denies potential phishing campaigns that impersonate their domains.
In addition, LockBit affiliates also use spam emails containing malicious documents, and they may use stolen credentials to gain access. To prevent these, it is crucial to demand the use of multi-factor authentication and to be cautious when opening any email attachments.
The most crucial step in preventing ransomware attacks is to keep offline backups. However, the group uses a double extortion model, stealing the victim’s data before encrypting it, making even offline backups insufficient to avoid paying the ransom. Organizations should be aware of any vulnerabilities in their environment to prevent this, which can be achieved with SOCRadar’s Attack Surface Management. This provides visibility into external-facing digital assets, allowing security teams to track vulnerabilities and limit the attack surface that ransomware operators may exploit.
CISA notes that LockBit affiliates take advantage of both old and new exploits, including:
See CISA’s Known Exploited Vulnerabilities (KEV) list for more information on mentioned vulnerabilities.
LockBit has been identified to use the following tools, as CISA lists:
IoCs from US Governmental Agencies’ #StopRansomware initiation report on LockBit 3.0;
File Sharing Sites:
Freeware and Open-Source Tools:
Mutex:
UAC Bypass via Elevated COM Interface:
Volume Shadow Copy Deletion:
Registry Artifacts:
Subscribe to our newsletter and stay updated on the latest insights!
PROTECTION OF PERSONAL DATA COOKIE POLICY FOR THE INTERNET SITE
Protecting your personal data is one of the core principles of our organization, SOCRadar, which operates the internet site (www.socradar.com). This Cookie Usage Policy (“Policy”) explains the types of cookies used and the conditions under which they are used to all website visitors and users.
Cookies are small text files stored on your computer or mobile device by the websites you visit.
Cookies are commonly used to provide you with a personalized experience while using a website, enhance the services offered, and improve your overall browsing experience, contributing to ease of use while navigating a website. If you prefer not to use cookies, you can delete or block them through your browser settings. However, please be aware that this may affect your usage of our website. Unless you change your cookie settings in your browser, we will assume that you accept the use of cookies on this site.
1. WHAT KIND OF DATA IS PROCESSED IN COOKIES?
Cookies on websites collect data related to your browsing and usage preferences on the device you use to visit the site, depending on their type. This data includes information about the pages you access, the services and products you explore, your preferred language choice, and other preferences.
2. WHAT ARE COOKIES AND WHAT ARE THEIR PURPOSES?
Cookies are small text files stored on your device or web server by the websites you visit through your browsers. These small text files, containing your preferred language and other settings, help us remember your preferences on your next visit and assist us in making improvements to our services to enhance your experience on the site. This way, you can have a better and more personalized user experience on your next visit.
The main purposes of using cookies on our Internet Site are as follows:
3. TYPES OF COOKIES USED ON OUR INTERNET SITE 3.1. Session Cookies
Session cookies ensure the smooth operation of the internet site during your visit. They are used for purposes such as ensuring the security and continuity of our sites and your visits. Session cookies are temporary cookies and are deleted when you close your browser; they are not permanent.
3.2. Persistent Cookies
These cookies are used to remember your preferences and are stored on your device through browsers. Persistent cookies remain stored on your device even after you close your browser or restart your computer. These cookies are stored in your browser’s subfolders until deleted from your browser’s settings. Some types of persistent cookies can be used to provide personalized recommendations based on your usage purposes.
With persistent cookies, when you revisit our website with the same device, the website checks if a cookie created by our website exists on your device. If so, it is understood that you have visited the site before, and the content to be presented to you is determined accordingly, offering you a better service.
3.3. Mandatory/Technical Cookies
Mandatory cookies are essential for the proper functioning of the visited internet site. The purpose of these cookies is to provide necessary services by ensuring the operation of the site. For example, they allow access to secure sections of the internet site, use of its features, and navigation.
3.4. Analytical Cookies
These cookies gather information about how the website is used, the frequency and number of visits, and show how visitors navigate to the site. The purpose of using these cookies is to improve the operation of the site, increase its performance, and determine general trend directions. They do not contain data that can identify visitors. For example, they show the number of error messages displayed or the most visited pages.
3.5. Functional Cookies
Functional cookies remember the choices made by visitors within the site and recall them during the next visit. The purpose of these cookies is to provide ease of use to visitors. For example, they prevent the need to re-enter the user’s password on each page visited by the site user.
3.6. Targeting/Advertising Cookies
They measure the effectiveness of advertisements shown to visitors and calculate how many times ads are displayed. The purpose of these cookies is to present personalized advertisements to visitors based on their interests.
Similarly, they determine the specific interests of visitors’ navigation and present appropriate content. For example, they prevent the same advertisement from being shown again to the visitor in a short period.
4. HOW TO MANAGE COOKIE PREFERENCES?
To change your preferences regarding the use of cookies, block or delete cookies, you only need to change your browser settings.
Many browsers offer options to accept or reject cookies, only accept certain types of cookies, or receive notifications from the browser when a website requests to store cookies on your device.
Also, it is possible to delete previously saved cookies from your browser.
If you disable or reject cookies, you may need to manually adjust some preferences, and certain features and services on the website may not work properly as we will not be able to recognize and associate with your account. You can change your browser settings by clicking on the relevant link from the table below.
5. EFFECTIVE DATE OF THE INTERNET SITE PRIVACY POLICY
The Internet Site Privacy Policy is dated The effective date of the Policy will be updated if the entire Policy or specific sections are renewed. The Privacy Policy is published on the Organization’s website (www.socradar.com) and made accessible to relevant individuals upon request.
SOCRadar
Address: 651 N Broad St, Suite 205 Middletown, DE 19709 USA
Phone: +1 (571) 249-4598
Email: [email protected]
Website: www.socradar.com
